Cloud Security: 5 Steps for Developing an Enterprise Cloud Strategy
Many organizations are paying an opportunity cost when it comes to the cloud – security teams tend to hold back due to cloud security worries.
Fears about security prevent their use of cloud services and organizations are not able to fully leverage the benefits of SaaS, PaaS, and IaaS.
What Is Cloud Security?
Much of the IT world continues to operate under the misconception about the security of public clouds – shared cloud infrastructure is risky.
This misconception reduces the ability of companies to take full advantage of the cost savings and flexibility of commercial cloud services.
The avoidance of cloud services can even lead to more security risks since organizations tend to rely on poorly managed in-house security systems with even more vulnerabilities.
While no technology – on premise or even cloud – is ever 100% secure or reliable, organizations can implement cloud security policies.
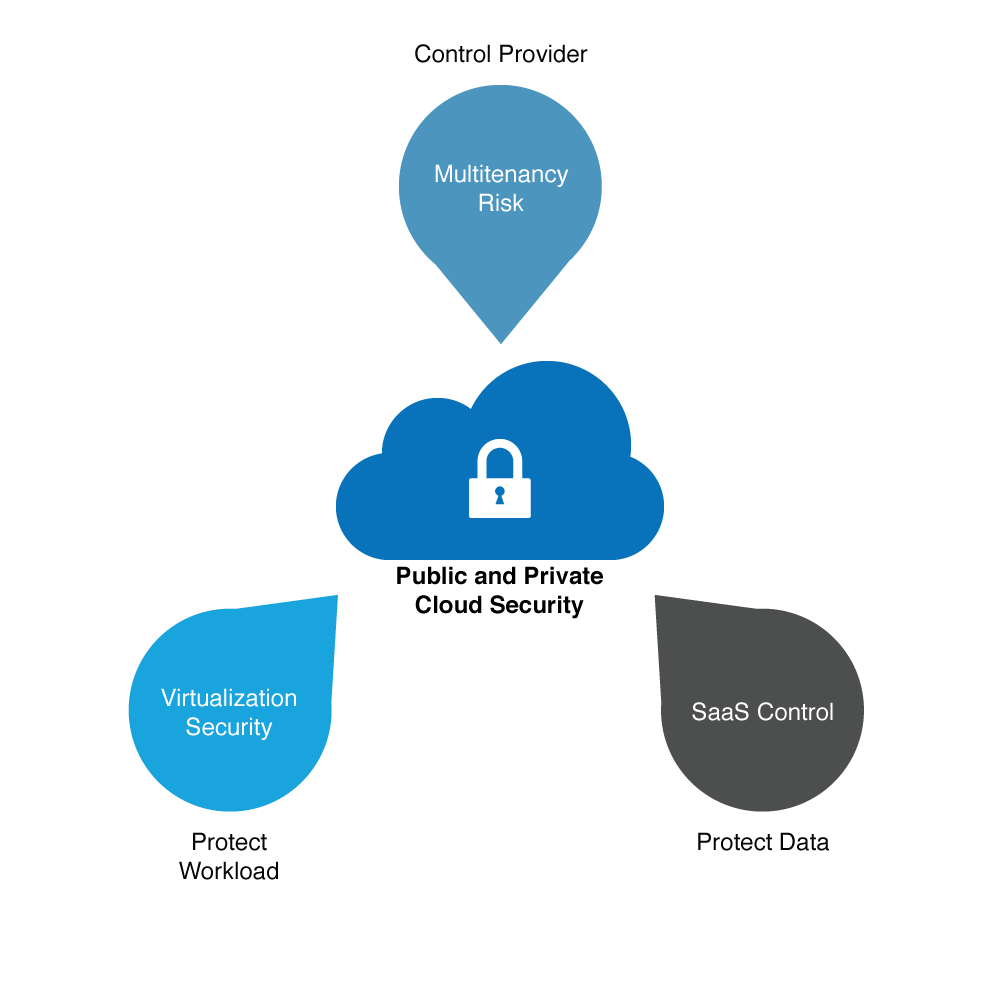
Cloud security is processes and policies that address security controls the provider puts in place to maintain data security, privacy, and compliance.
Cloud security also incorporates a data backup plan in the case of a cloud security breach.
Organizations that have the most success with cloud security have been able to address the considerations of IaaS workload security, SaaS control, and cloud management and provider management.
Why is Cloud Security Important?
Every organization whether small or large is at risk of losing all its confidential data to a hacking attempt. Hence, cloud security presents itself as a means of protecting all the data of a company. The best part about cloud security is that documents can be accessed anywhere, anytime, and from any device. All you need to do is pass the security check. This not only reduces paperwork but also keeps your documents secured in a centralized location for as long as you want.
There are repercussions surrounding the security provided by cloud services, but it is indeed way better than your in-house security system. Hence, investing in a cloud security system is one of the best ways to keep your documents secure.
What Are the Benefits of Utilizing an Enterprise Cloud Strategy?
When a cloud security service is provided, an enterprise cloud strategy is introduced. This is done to make sure that there is no breach of information and that people who can access confidential documents are taken into consideration. So let’s see what benefits enterprise cloud strategy provides.
- With automatic updates, hence you do not need to spend on buying the latest software to ensure security
- Provides advanced security and there is a very meager chance of data getting hacked
- Documents can be accessed anywhere, anytime, and from any device
- End user experience is improved by flawless online service
- Provides scalability by allowing you to choose the data plan depending on your company’s requirements
Developing an Enterprise Cloud Strategy
The most important step an organization can take to develop enterprise cloud security is for corporate leadership to understand that cloud computing is indispensable and needs to be managed through planning and policy.
1. Develop a Strategy
Develop a strategy for cloud use and management, including what can be placed into the cloud and under what circumstances.
Most organizations have cloud strategies that lag way behind cloud use, meaning there is a large amount of unsanctioned or unrecognized cloud use.
2. Implement and Enforce Policies
Implement and enforce policies on cloud ownership, responsibility, and risk acceptance by establishing expectations of cloud use.
Every organization should maintain an inventory of the cloud services currently in use, and track the ownership and employees responsible.
At the end of the day, no organizational process can be properly undertaken and reliably used unless the responsibility is explicit and enforced.
Interested in Cloud Security? Check out this free whitepaper on how to ensure complete print security in the Cloud.
3. Follow a Life Cycle
Follow a life cycle to cloud governance that focuses on operational control of the SaaS, PaaS, and IaaS services.
Public cloud use requires regular attention to the status and performance of cloud service providers performing processes deemed critical.
While most enterprises concentrate on risk acceptance, other stages of the life cycle such as implementation, requirements analysis, continuous management, and end of life are stages that require more attention.
4. Develop organizational expertise
Develop organization expertise for the implementation and control of the different cloud models you will be using.
Many organizations are struggling to understand security knowledge fully, and many knowledge gaps are present as each IaaS service has its own user interface and vendor-specific characteristics.
A successful approach must allocate resources to the development of skills to ensure all cloud use cases are secure and compliant.
5. Implement Central Management and Monitoring
Implement central management and monitoring to overcome the complexities of the cloud.
One of the downsides of the cloud is the complexities of different solutions, which leads to management inefficiencies.
Enterprises can implement third party multi-function control tools to integrate multiple public and hybrid clouds and ensure they are all compliant and meeting security expectations.
Without an enterprise cloud security strategy, CIO’s, CTO’s and other IT leaders feel uneasy about the use of the cloud.
Taking a top down approach to cloud security provides guidance on how the cloud should be used, and what needs to be done to ensure security and control of current and future cloud services.
Check out our FREE whitepaper on Secure Cloud Printing below to learn how you can complement your Cloud Security strategy.
Try UniPrint InfinityCloud
Whether you are printing at the office or at home, UniPrint InfinityCloud is the cloud printing solution of choice for your organization.
Recent Posts
- Cloud Printing Management: The Secret to Fewer Help Desk Tickets
- Why Should You Outsource Printing Management? A Comprehensive Overview
- How Cloud Print Management Prevents Print Server Vulnerabilities
- Is Printing Dead?
- How InfinityCloud Outshines Microsoft Universal Print in 2024
- How the Cloud Print Management Software Drives Sustainable Business Practices
- How Cloud Print Management Enhances Your Network Security
- How to Enhance Remote Work Experience with Secure Serverless Printing
- Update to Google Drive Cloud Storage
- A Guide to Preventing Phishing Attacks
- See All