Printer Hacking – A Very Real Enterprise Data Security Breach
In today’s immersive world of technology, organizations have access to an array of tools used to assist them in every-day operations and decision making.
As we innovate and pioneer technology, we also create a new set of issues.
Data breaches, data theft, phishing, ransomware, and malware are all good examples.
Many of these vulnerabilities can come from every-day usage of peripherals like printers, and it is something enterprises must consider to protect the confidentiality of their documents.
Early in 2017, a white-hat hacker breached over 150,000 office and receipt printers to raise everyone’s awareness on ensuring organizations have secure printing on all their printers.
Widely recognized printers such as HP, Brother, Epson and Canon were prone to attacks.
The hacker Stackoverflowin, states that the script he wrote “targets printing devices that have IPP (Internet Printing Protocol) ports, LPD (Line Printer Daemon) ports, and port 9100 left open to external connections.”
Printers set-up in an organization by default have no security.
A network administrator must reconfigure the network to keep it secure.
The usage of multi-purpose printers or MFPs are prominent in small to large organizations because of how easy it makes day-to-day operations.
Features like faxing, scanning, photocopying and emailing have proven fruitful in cutting down time and costs.
However, the problem with that is that it opens a multitude of security vulnerabilities.
Printer Hacking Security Breaches
How do attacks happen?
There are several ways hackers can perform malicious activities.
A common attack is when MFPs have an authentication mechanism that gives access to an employee via RFID, swipe-card, fingerprint, or manual entry of credentials (username and password).
Hackers can bypass the MFPs network access granting them the ability to print jobs and steal sensitive information.
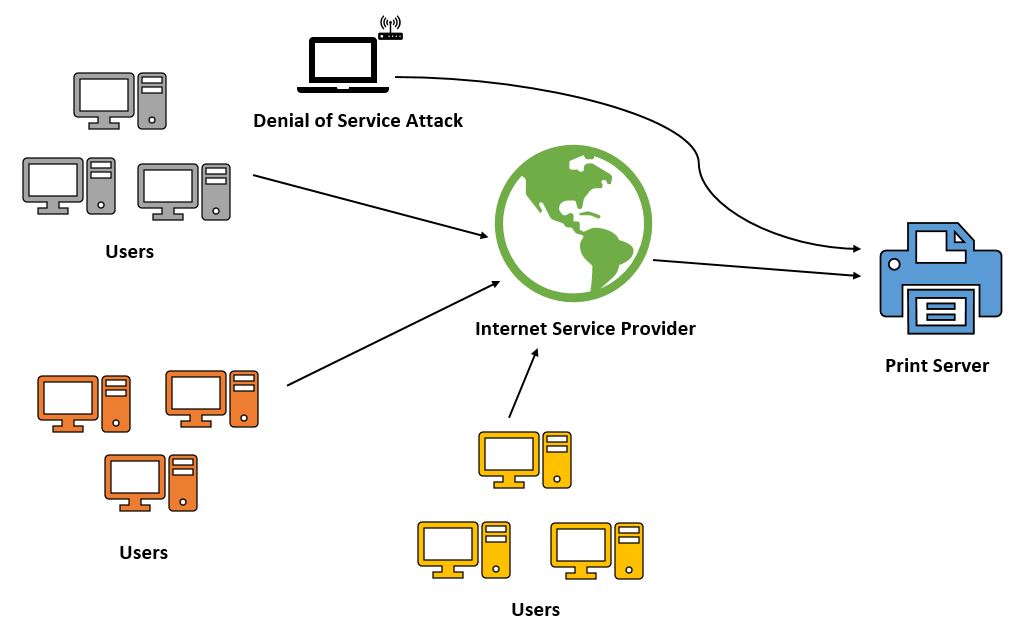
Another popular attack is a denial of service or DOS for short.
It is when a printer is flooded with traffic from a botnet or an application that would render the printer useless, sometimes going as far as destroying it.
Obtaining free or cheap software for conducting a DOS attack is not hard.
Searching for results on Google or the “dark-web” (a digital black marketplace) is enough.
The emergence of BYOD and printing has made organizations even more vulnerable to print attacks.
Many personal devices are connected to a printer, or an array of printers.
A hacker can inject your personal device with malware that can gain direct access to the corporate network, and thus its printers.
Interested in learning more about how to secure your print infrastructure? Check out this free whitepaper on how to achieve a secure print infrastructure!
Printer Hacking Security Measures
There are many security measures that your organization can use to avoid attacks on printers.
Allow communications only with secured or trusted networks and hosts.
The network administrator can easily configure which websites employees have access too. Get rid of unused protocols such as FTP, telnet and SNMP.
Turning off unused protocols limits the way malware, viruses and worms can get inside the organizational network.
Use a corporate-only network address for keeping the printer hidden from the internet.
Although hiding organizational printers will certainly keep the spotlight away, it does not necessarily mean your printers are secured.
If a curious hacker manages to penetrate the network, he or she will be able to see the printer.
If there is no security measure on the printers, then it will be easy for a hacker to intercept documents, steal sensitive information or sabotage its operations.
As the digital world grows to solve every-day tasks in the lives of millions, so does the need of cyber-security.
It is progressively becoming easier to breach devices and steal sensitive information. In today’s global space, organizations have an obligation to deploy printer related security measures.
Try UniPrint InfinityCloud
Whether you are printing at the office or at home, UniPrint InfinityCloud is the cloud printing solution of choice for your organization.
Recent Posts
- How Cloud Print Management Prevents Print Server Vulnerabilities
- Is Printing Dead?
- How InfinityCloud Outshines Microsoft Universal Print in 2024
- How the Cloud Print Management Software Drives Sustainable Business Practices
- How Cloud Print Management Enhances Your Network Security
- How to Enhance Remote Work Experience with Secure Serverless Printing
- Update to Google Drive Cloud Storage
- A Guide to Preventing Phishing Attacks
- Level up your Microsoft Universal Printing experience with PF 360 Print
- How To Fix 10 Common Printer Problems
- See All